FraudLoad |
General
MD5: 849d9354fcb78b9ecd0cbabb84a23b43
SHA1: cd278632b61e1632044a6d58ddb42aeab334d5e8
SHA256: 08d4c8a6e51437049647aa0d65ed32b5b49f0d91f80b1d60d9ea8c50692c86be
ssdeep: 1536:FhJXAdNwpd0Nf6P62rh6/hur7TjdhCEhcd:FjwdNqsfe6Yh0hgTLN0
FileSize: 56 kB
FileType: Win32 EXE
MachineType: Intel 386 or later, and compatibles
OSVersion: 5.1
PEType: PE32
Subsystem: Windows GUI
SubsystemVersion: 4.0
[[ 3 section(s) ]]
name, viradd, virsiz, rawdsiz, ntropy, md5
UPX0, 0x1000, 0x12000, 0x0, 0.00, d41d8cd98f00b204e9800998ecf8427e
UPX1, 0x13000, 0xB000, 0xB000, 7.88, 5be537ab121bdb25172c7bbcf7add5bc
.rsrc, 0x1E000, 0x2000, 0x1C00, 5.47, d43b2051bad6099ef9f41604aad4a0b0
[[ 7 import(s) ]]
KERNEL32.DLL: LoadLibraryA, GetProcAddress, VirtualProtect, VirtualAlloc, VirtualFree, ExitProcess
ADVAPI32.dll: AddAce
MSVCRT.dll: atol
ole32.dll: CoCreateGuid
oleaut32.dll: VariantInit
RPCRT4.dll: UuidCreate
USER32.dll: GetDC
Deteccion:
39/ 41 (95.1%)
| Antivirus | Version | Last Update | Result |
|---|
| AhnLab-V3 | 2011.03.23.01 | 2011.03.23 | Win-Trojan/Fraudload.56832.AF |
| AntiVir | 7.11.5.43 | 2011.03.23 | TR/Dldr.FakeAle.kon |
| Antiy-AVL | 2.0.3.7 | 2011.03.22 | Trojan/Win32.FraudLoad.gen |
| Avast | 4.8.1351.0 | 2011.03.23 | Win32:Malware-gen |
| Avast5 | 5.0.677.0 | 2011.03.23 | Win32:Malware-gen |
| AVG | 10.0.0.1190 | 2011.03.23 | Downloader.Generic9.CHRY |
| BitDefender | 7.2 | 2011.03.23 | Trojan.Generic.3231804 |
| CAT-QuickHeal | 11.00 | 2011.03.23 | TrojanDownloader.FraudLoad.gm |
| ClamAV | 0.96.4.0 | 2011.03.23 | Trojan.Downloader-89625 |
| Commtouch | 5.2.11.5 | 2011.03.22 | W32/FraudLoad.C!Generic |
| Comodo | 8073 | 2011.03.23 | MalCrypt.Indus! |
| DrWeb | 5.0.2.03300 | 2011.03.23 | Trojan.Fakealert.12876 |
| eSafe | 7.0.17.0 | 2011.03.22 | Win32.TRDldr.FakeAle |
| eTrust-Vet | 36.1.8231 | 2011.03.23 | Win32/Securityessentials2010.F |
| F-Prot | 4.6.2.117 | 2011.03.22 | W32/FraudLoad.C!Generic |
| F-Secure | 9.0.16440.0 | 2011.03.23 | Trojan.Generic.3231804 |
| Fortinet | 4.2.254.0 | 2011.03.23 | - |
| GData | 21 | 2011.03.23 | Trojan.Generic.3231804 |
| Ikarus | T3.1.1.97.0 | 2011.03.23 | Trojan.Win32.FakeAV |
| Jiangmin | 13.0.900 | 2011.03.23 | TrojanDownloader.FraudLoad.lri |
| K7AntiVirus | 9.94.4188 | 2011.03.23 | Trojan |
| McAfee | 5.400.0.1158 | 2011.03.23 | Downloader-CFA |
| McAfee-GW-Edition | 2010.1C | 2011.03.23 | Downloader-CFA |
| Microsoft | 1.6603 | 2011.03.23 | Rogue:Win32/Fakeinit |
| NOD32 | 5977 | 2011.03.23 | Win32/TrojanDownloader.FakeAlert.AED |
| Norman | 6.07.03 | 2011.03.22 | W32/Fakeinit.V |
| nProtect | 2011-02-10.01 | 2011.02.15 | Trojan-Downloader/W32.FraudLoad.56832.R |
| Panda | 10.0.3.5 | 2011.03.22 | Adware/SecurityEssentials2010 |
| PCTools | 7.0.3.5 | 2011.03.21 | RogueAntiSpyware.CoreGuardAntivirus2009!rem |
| Prevx | 3.0 | 2011.03.26 | Medium Risk Malware |
| Rising | 23.50.01.06 | 2011.03.22 | Suspicious |
| Sophos | 4.63.0 | 2011.03.23 | Mal/FakeAV-BW |
| SUPERAntiSpyware | 4.40.0.1006 | 2011.03.23 | - |
| Symantec | 20101.3.0.103 | 2011.03.23 | CoreGuardAntivirus2009 |
| TheHacker | 6.7.0.1.155 | 2011.03.23 | Trojan/Downloader.FakeAlert.aed |
| TrendMicro | 9.200.0.1012 | 2011.03.23 | TROJ_OFICLA.SM |
| TrendMicro-HouseCall | 9.200.0.1012 | 2011.03.23 | TROJ_OFICLA.SM |
| VBA32 | 3.12.14.3 | 2011.03.23 | Trojan-Downloader.Win32.FraudLoad.gmc |
| VIPRE | 8790 | 2011.03.23 | VirTool.Win32.Obfuscator.hg!b (v) |
| ViRobot | 2011.3.23.4372 | 2011.03.23 | Trojan.Win32.Fakeinit.56832 |
| VirusBuster | 13.6.264.0 | 2011.03.22 | Trojan.DL.FakeAle!y3okK0g8nR8 |
*Gracias a VirusTotal
Uso de Packer, Crypter, Binder: SI
TrID:
UPX compressed Win32 Executable (38.5%)
Win32 EXE Yoda's Crypter (33.5%)
Win32 Executable Generic (10.7%)
Win32 Dynamic Link Library (generic) (9.5%)
Clipper DOS Executable (2.5%)
|
|
Strings dentro del ejecutable: Archivo TXT
» GetExitCodeProcess
» FlushFileBuffers
» LockResource
» FindFirstFileW
» CreateEventW
» LoadLibraryExA
» GetTickCount
» lstrcatW
» VirtualAlloc
» FindResourceA
Comportamiento General
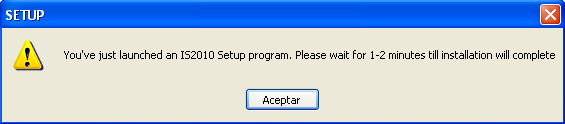
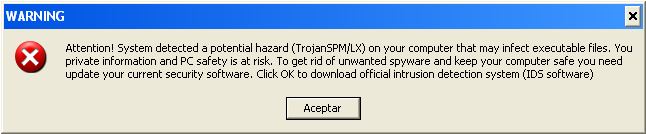
1. Al ejecutar el archivo se muestra el siguiente mensaje:
|
|
|
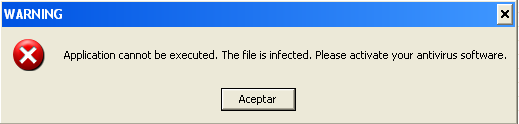
2. Después de un periodo de tiempo el virus cierra todos los programas e impide abrirlos de nuevo mostrando el siguiente mensaje:
|
|
|
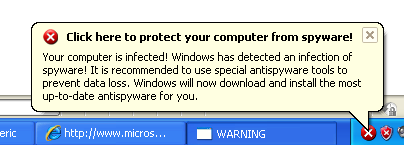
3. Al abrir el Internet Explorer se muestran los siguientes mensajes:
|
|
Modificaciones en el Registro de Windows: Archivo TXT
----------------------------------
Keys added
----------------------------------
HKLM\SOFTWARE\Microsoft\Internet Explorer\PhishingFilter
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains\buy-security-essentials.com
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains\get-key-se10.com
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_RASMAN\0000\Control
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_TAPISRV\0000\Control
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_RASMAN\0000\Control
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_TAPISRV\0000\Control
HKU\S-1-5-21-2000478354-839522115-725345543-500\Software\Microsoft\Internet Explorer\PhishingFilter
HKU\S-1-5-21-2000478354-839522115-725345543-500\Software\Microsoft\Windows\CurrentVersion\Explorer\BitBucket\c
HKU\S-1-5-21-2000478354-839522115-725345543-500\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains\buy-security-essentials.com
HKU\S-1-5-21-2000478354-839522115-725345543-500\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains\download-soft-package.com
HKU\S-1-5-21-2000478354-839522115-725345543-500\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains\download-software-package.com
HKU\S-1-5-21-2000478354-839522115-725345543-500\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains\get-key-se10.com
HKU\S-1-5-21-2000478354-839522115-725345543-500\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains\is-software-download.com
----------------------------------
Values added
----------------------------------
HKLM\SOFTWARE\Microsoft\Internet Explorer\PhishingFilter\EnabledV8: 0x00000000
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains\buy-security-essentials.com\http: 0x00000002
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains\get-key-se10.com\http: 0x00000002
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\EnableLUA: 0x00000000
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\smss32.exe: "C:\WINDOWS\system32\smss32.exe"
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_RASMAN\0000\Control\ActiveService: "RasMan"
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_TAPISRV\0000\Control\ActiveService: "TapiSrv"
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_RASMAN\0000\Control\ActiveService: "RasMan"
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_TAPISRV\0000\Control\ActiveService: "TapiSrv"
HKU\S-1-5-21-2000478354-839522115-725345543-500\Software\8636065b-fef0-4255-b14f-54639f7900a4: "8636065b-fef0-4255-b14f-54639f7900a4"
HKU\S-1-5-21-2000478354-839522115-725345543-500\Software\Microsoft\Internet Explorer\PhishingFilter\Enabled: 0x00000000
HKU\S-1-5-21-2000478354-839522115-725345543-500\Software\Microsoft\Internet Explorer\PhishingFilter\EnabledV8: 0x00000000
HKU\S-1-5-21-2000478354-839522115-725345543-500\Software\Microsoft\Windows\CurrentVersion\Explorer\EnableAutoTray: 0x00000000
HKU\S-1-5-21-2000478354-839522115-725345543-500\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains\is-software-download.com\http: 0x00000002
HKU\S-1-5-21-2000478354-839522115-725345543-500\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains\get-key-se10.com\http: 0x00000002
HKU\S-1-5-21-2000478354-839522115-725345543-500\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains\download-software-package.com\http: 0x00000002
HKU\S-1-5-21-2000478354-839522115-725345543-500\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains\download-soft-package.com\http: 0x00000002
HKU\S-1-5-21-2000478354-839522115-725345543-500\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains\buy-security-essentials.com\http: 0x00000002
HKU\S-1-5-21-2000478354-839522115-725345543-500\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\2\Flag: 0x00000043
HKU\S-1-5-21-2000478354-839522115-725345543-500\Software\Microsoft\Windows\CurrentVersion\Run\smss32.exe: "C:\WINDOWS\system32\smss32.exe"
----------------------------------
Values modified
----------------------------------
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit: "C:\WINDOWS\system32\userinit.exe,"
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit: "C:\WINDOWS\system32\winlogon32.exe"
Conexiones HTTP: SI
A través de un servidor DNS especial para la prueba podemos analizar algunos de los contenidos de los paquetes enviados:
|
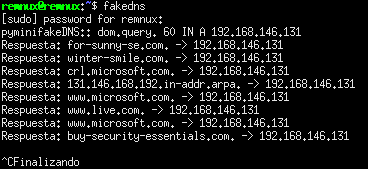
|
|
http://for-sunny-se-com/loads.php?code=03
|
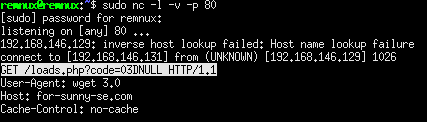
|
|
http://buy-security-essentials.com/buy/?code=03
|
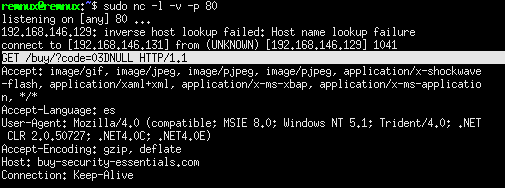
|
Servidores con los cuales se establencen conexiones:
| Domain Name | ICANN Registrar | IP Address | IP Location | Origin |
|---|
| for-sunny-se.com | FINDYOUADOMAIN.COM LLC | 208.73.210.29 | California - Los Angeles - Oversee.net |  |
| winter-smile.com | EUROPEANCONNECTIONONLINE.COM LLC | 208.73.210.29 | California - Los Angeles - Oversee.net |  |
| is-software-download.com | - | - | - | - |
| get-key-se10.com | - | - | - | - |
| download-software-package.com | - | - | - | - |
| download-soft-package.com | - | - | - | - |
| buy-security-essentials.com | - | - | - | - |
|
| | | | |
